AWS SSO integration
User authentication
Create an Amazon SSO application
Inside the Applications page of the AWS SSO dashboard, click the Add New Application button.
Within the Add New Application page, click Add a Custom SAML 2.0 Application.
You will see a form like:
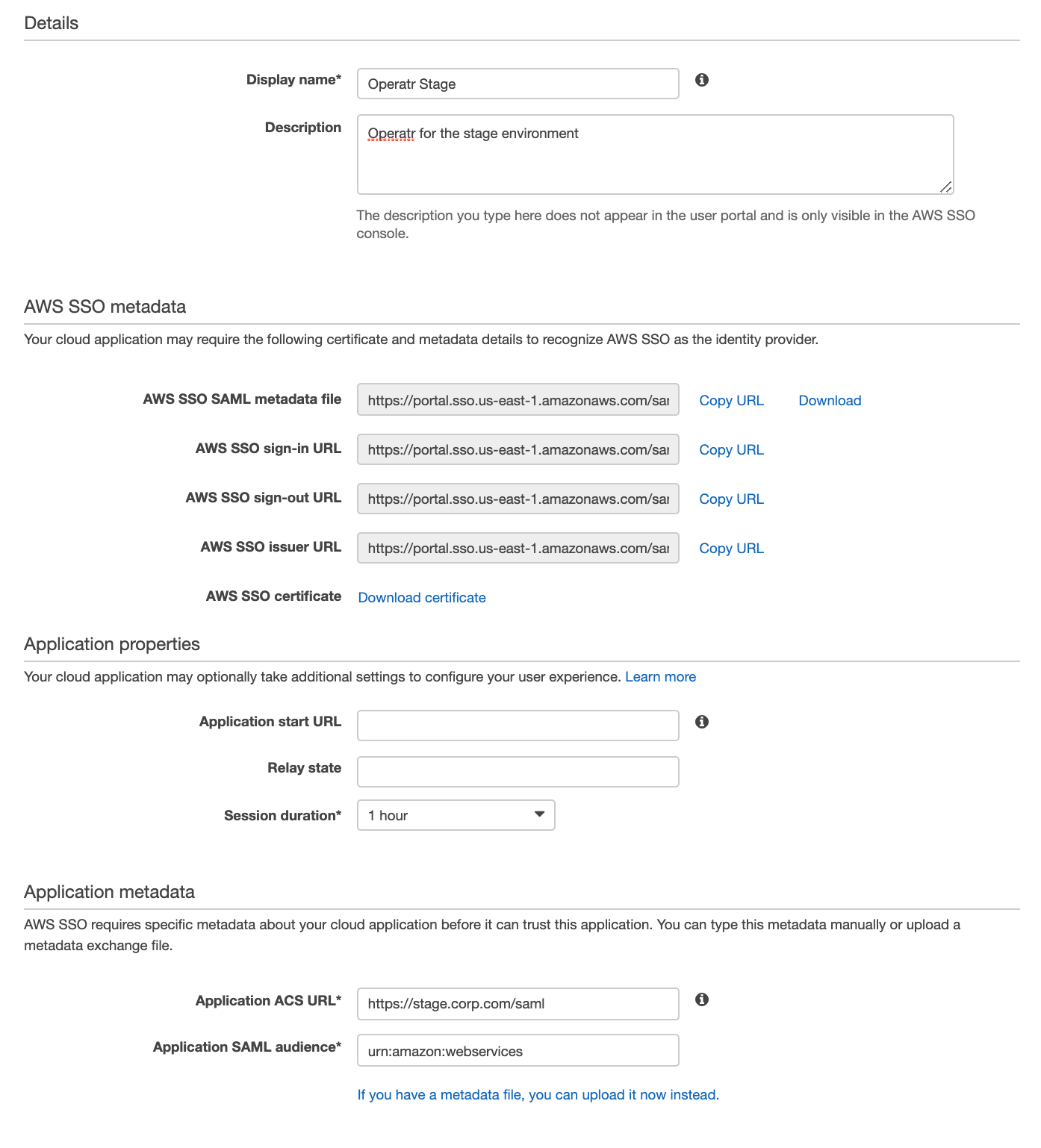
Application Details
- Display Name: set this to a suitable name for the instance you are securing, e.g. Flex-UAT-1.
- Description: the description of the application.
AWS SSO Metadata
Download the AWS SSO SAML metadata file and optionally the AWS SSO Certificate, these files will be used later to configure Flex.
Application Properties
- Session Duration: Set to a value that makes sense for your users and security policies.
- Relay State: Leave empty.
- Application Start URL: Optional, can be left empty.
Application Metadata
Select the option to manually type metadata values.
- Application ACS URL: Absolute path to your Flex, e.g. https://kpow.corp.com/saml
- Application SMAL Audience: set to urn:amazon:webservices
Integrate Flex with AWS SSO
Set the following environment variables and start Flex.
AUTH_PROVIDER_TYPE=saml
SAML_RELYING_PARTY_IDENTIFIER=[Display Name]
SAML_ACS_URL=[Application ACS URL]
SAML_METADATA_FILE=[path to downloaded AWS SSO SAML metadata file]
# Optional
SAML_CERT=[path to the AWS SSO Certificate .pem file]
Flex will now authenticate users with AWS SSO.
User authorization
See the guide to Role Based Access Control for full configuration details.
Integrate AWS SSO and Flex RBAC
Edit the Flex application within the AWS SSO dashboard and navigate to "Attribute Mappings".
Add the following Roles mapping to ${user:groups}

In this case we are using a user's assigned groups as their role for Flex RBAC configuration.
Each of the Roles in this example will have the value of the GUID of the AWS SSO group.
If you are using AWS SSO with Active Directory you may find the Group SID from AD in place of the AWS SSO Group GUID in ${user:groups}
You can find the AWS SSO Group GUID from the AWS console in the URL params:

If you are using Active Directory or an external IdP as your identity source for AWS SSO you can use a supported directory attribute like {dir:....} to map attributes from AD to AWS SSO. For more info visit the AWS documentation.