Okta
This integration configures OpenID Connect as the authentication mechanism with Okta as the identity provider (IdP) and Kpow as the relying party.
Create an Okta OpenID application
-
Login to your Okta account.
-
Navigate to Admin > Applications > Create App Integration
-
In Create a New Application Integration popup set these values and click Create:
- Sign on method: OIDC - OpenID Connect
- Application type: Web Application
-
In Create OpenID Connect Integration set these values and click Save:
- App integration name: The name of your Kpow instance, e.g. 'Kpow Staging'.
- Sign-in redirect URIs: The absolute Kpow callback URI, e.g.
https://kpow.stage.mycorp.com/oauth2/okta/callback - Sign-out redirect URIs: The absolute URI of where Kpow is hosted, e.g.
https://kpow.stage.mycorp.com
-
Click Save and next you will be redirected to the applications settings page.
-
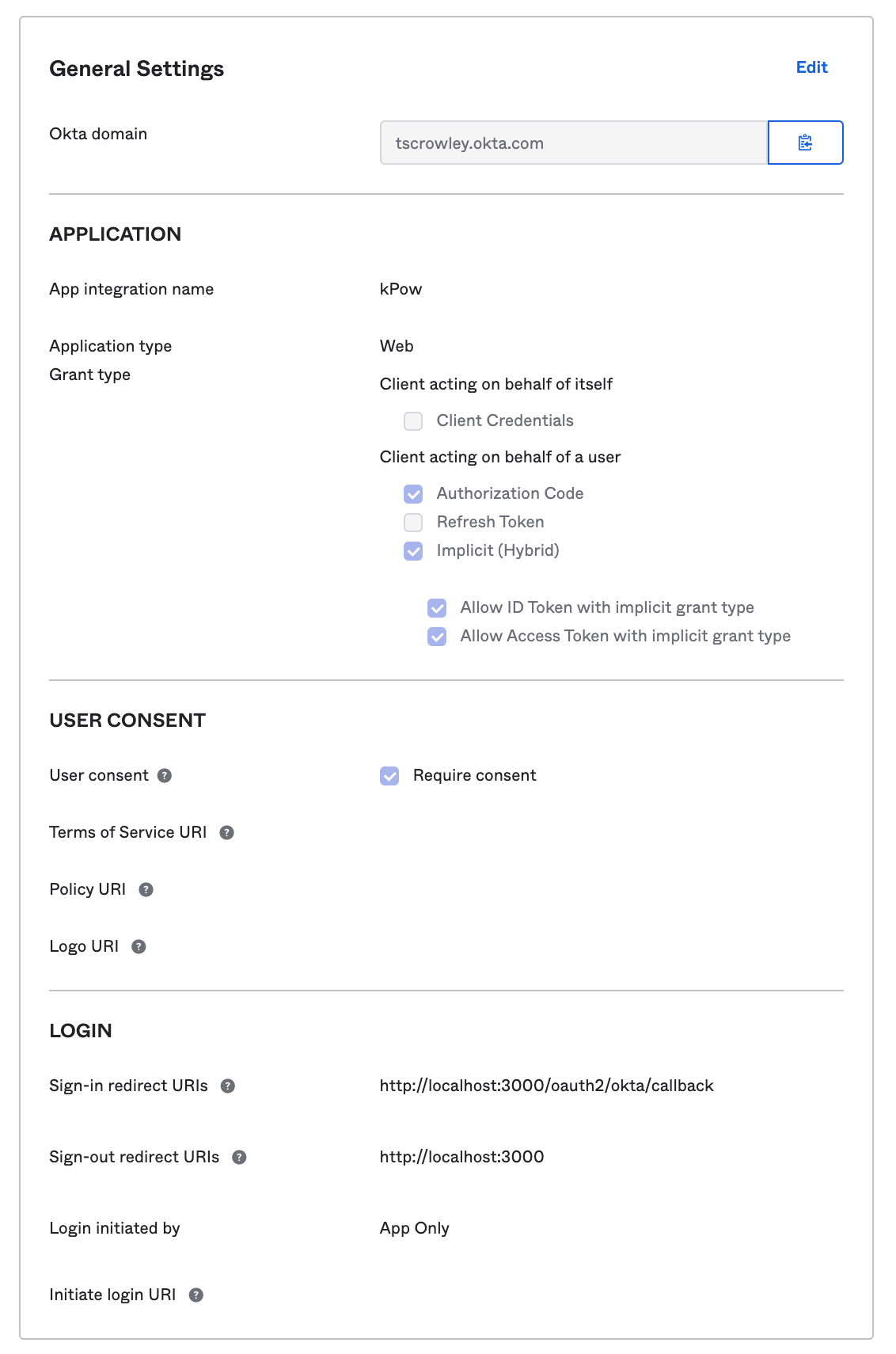
Navigate to General Settings > Edit, and configure:
Initiate login URI: The absolute Kpow login URI, e.g:
https://kpow.stage.mycorp.com/oauth2/oktaOptionally, if you would like Okta to appear in your organization's list of Okta apps:
- Login initiated by: "Either Okta or App" selected.
- Application visibility:
- "Display application icon to users" selected.
- "Display application icon in the Okta Mobile app" selected.
- Allowed grant types:
- "Implicit (Hybrid)" selected.
- "Allow ID Token with implicit grant type" selected.
- "Allow Access Token with implicit grant type" selected.
- "Implicit (Hybrid)" selected.
-
Make note of the Client Credentials section that appears below.
-
Click Assignments and assign users to Kpow.
Integrate Kpow with Okta OpenID
Set the following environment variables and start Kpow:
-
AUTH_PROVIDER_TYPE=okta -
OKTA_ORGANISATION=the name of your Okta organization, e.g. mycorp -
OPENID_CLIENT_ID=the Client ID found in Client Credentials. -
OPENID_CLIENT_SECRET=the Client Secret found in Client Credentials. -
AUTH_LANDING_URI=The absolute Kpow URI, e.g:https://kpow.stage.mycorp.com
Kpow will now authenticate users with Okta (OpenID).
User authorization (RBAC)
See the guide to Role Based Access Control for full configuration details.
Integration
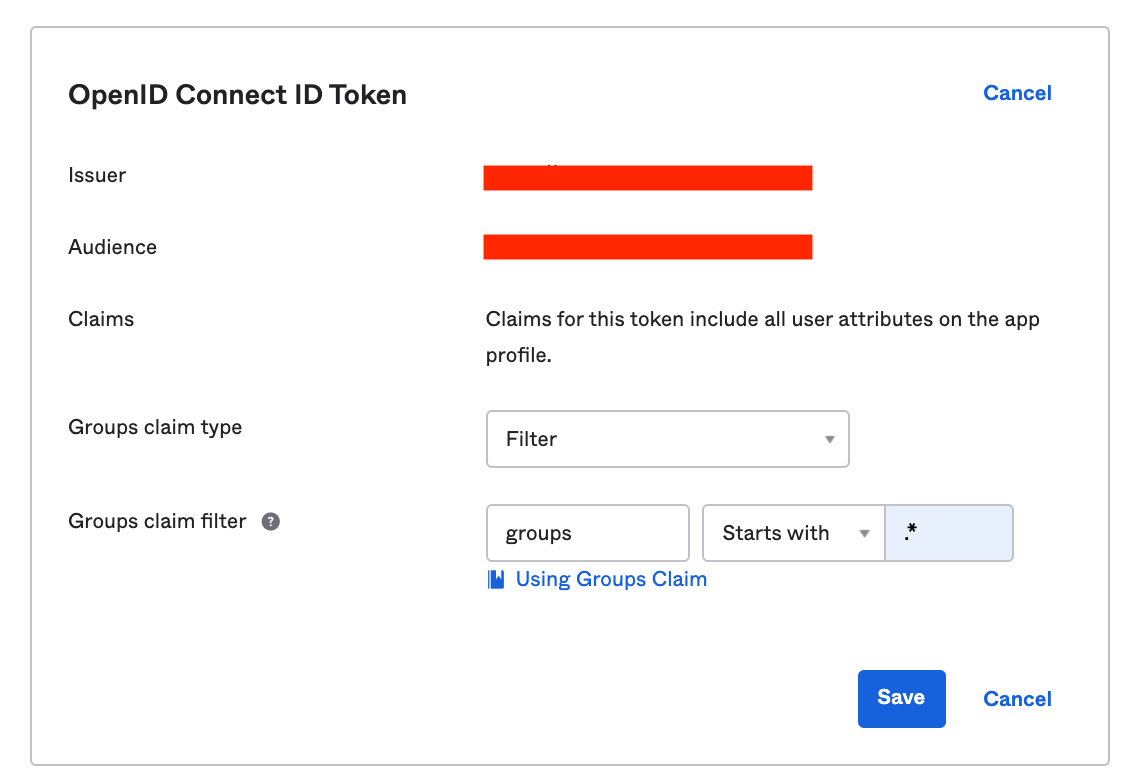
When RBAC is enabled Kpow will request groups scope to view the groups associated with an authenticated user. Kpow considers Okta groups as roles in your RBAC configuration.
You will need to configure a relevant group claim filter for the Kpow OpenID integration.
To match all groups use either 'Starts with' or 'Matches regex' and '.*'